Tom7-inline-bridge
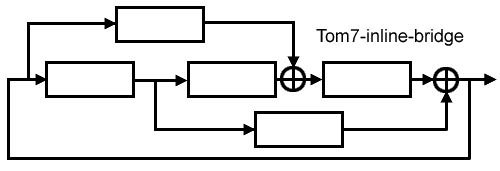 This is a construction for inline generators (bit generators
which take input) which combines five generators to increase the complexity
of the system. The construction can either operate in generator or inline
generator mode (taking input or not).
The idea is to have three inline generators in series, a fourth parallel
to the first two, and the fifth parallel to the second two. The output is
recombined using an exclusive or operation.
The device as pictured above has self-feedback. The input to the two
left generators could be replaced by an input, making the entire
construction an inline generator.
Using my program stat, this produces
well-distributed pseudorandom bits on the example initial state. This
is not surprising, for the output of the final skipstate generator should
be well distributed regardless of the input.
This should definitely be at least as secure as each generator. However,
even knowing one of the generators does not give you much; the parallelizing
seems to make it very difficult to correlate the effects of each bit.
The weakest part of this might be the feedback mechanism; if you know
the output stream then you know the input feedback. Operating this in
inline-generator mode would of course alleviate that problem.
The use of different inline generators (skipstate LFSRs are used below).
Expanding this to patterns which include more generators.
Feedback within the device (this seems to make it less elegant).
/*
C Implementation of a Tom7-bridge device using skipstate LFSRs.
This code is distributed under the GNU public license;
see http://www.gnu.org/copyleft/gpl.html.
I can't make any claims about the security of this algorithm because
I am not a trained cryptographer, though it produces (as far as I can
tell) statistically random output. This code should be thought about,
but not used unless you know more about this than me.
Tom 7
http://tom7.org/
*/
#include
Back to Tom's Cryptography Thingie.
|